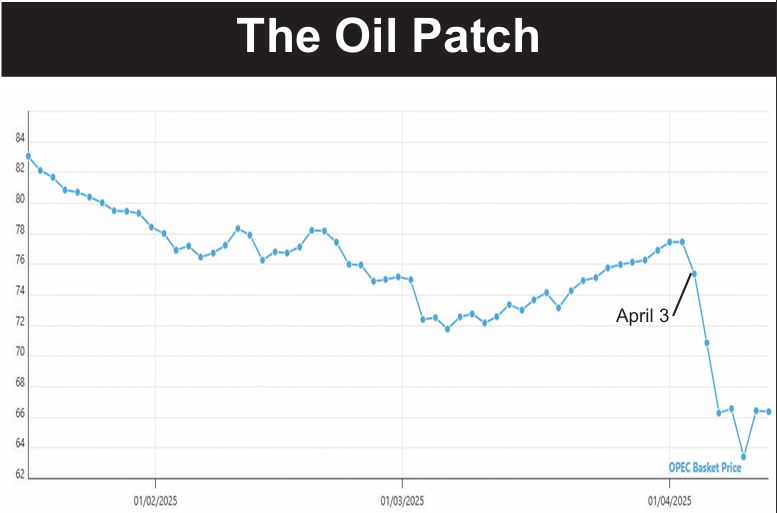
and try to wheedle information out of them with seemingly innocent email queries.
A description of Iranian cyber spying activities appears in a 2009 State Department cable that The Washington Times last week found amidst the massive download of a quarter million classified documents that WikiLeaks posted a month ago.
The cable highlights an Iranian espionage campaign aimed at gathering military and technology data through the Internet and emails.
The March 31, 2009, cable, labeled “secret,” identified several Iranian institutions that engage in collection against the US government—including the highly respected Amirkabir University of Technology.
Some of the data obtained by the Iranians could be used to conduct cyber attacks on he United States in the future, the cable said.
From 2007 to 2009, addresses connected to Iran’s Farhang Azma Communication Co. directly browsed a number of US Navy unit websites and systematically downloaded more than 100 Navy unit webpages, the cable said. This is all public information. It isn’t clear what purpose this collection effort served, though it would help researchers learn more about how the Navy is organized and functions.
The cable said students and researchers at a number of prominent Iranian universities and companies had targeted US information for several years. The cable said the methods used include attempts by people from Iranian universities and commercial organizations to solicit data from US contractors engaged in classified work through “socially engineered email messages” that targeted restricted US operations and research. In other words, the emailers were trying to befriend and innocently extract classified information from these Americans.
“This information could then be used to develop similar programs for the [government of Iran], shared with third-party entities (e.g., Islamic extremist groups), or exploited through additional Iranian computer network operations activities,” the cable said.
The Iranians also searched for digital information on US facilities in Iraq and Afghanistan, as well as on vehicles, vessels and people.
Two universities that are part of the Iranian cyber-spying operation were identified as Amirkabir University of Technology and Malek Ashtar University of Technology in Tehran. Malek Ashtar was founded by the Pasdaran after the revolution, but Amirkabir is a long established and respected institution.
The institutions spied on “a number of highly sophisticated technology projects, particularly those related to unmanned aerial vehicles (UAVs) and autonomous underwater vehicles,” the cable says. The Islamic Republic has said these areas of technology are a high priority for the military.
The Esfahan University of Technology also tried to obtain US technology, according to the cable.
The cable warned that in addition to losing military and commercial technology to Iran, the cyber-spying could be supplied by the Iranians to “state-sponsored and independent actors [who] may seek to gather information in order to hinder the success of constructive discourse or attempt to exploit individuals involved.”
This suggested the Iranians were trying to find embarrassing information about Americans engaged in classified technology that could then be used to induce those people to provide the classified data to Iran to avoid exposure.