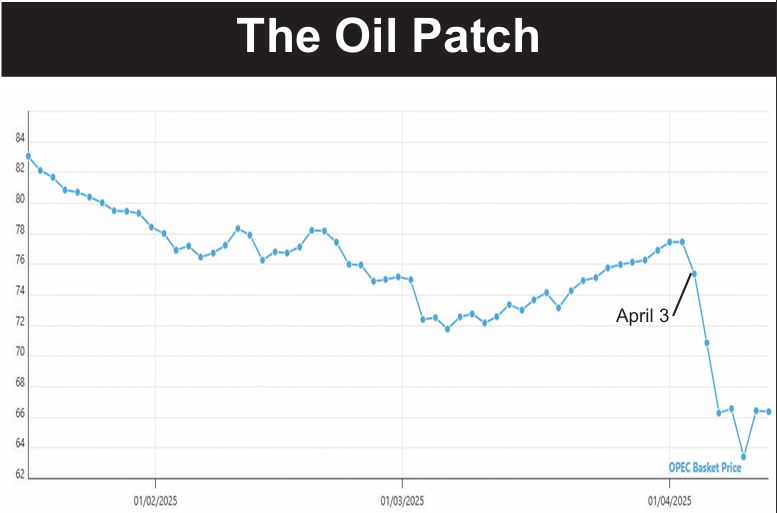
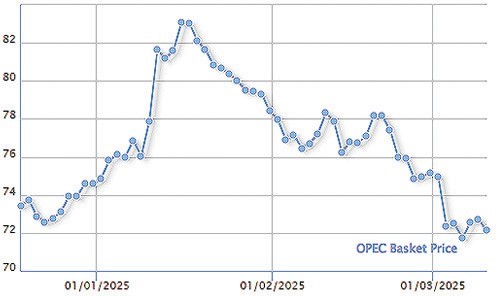
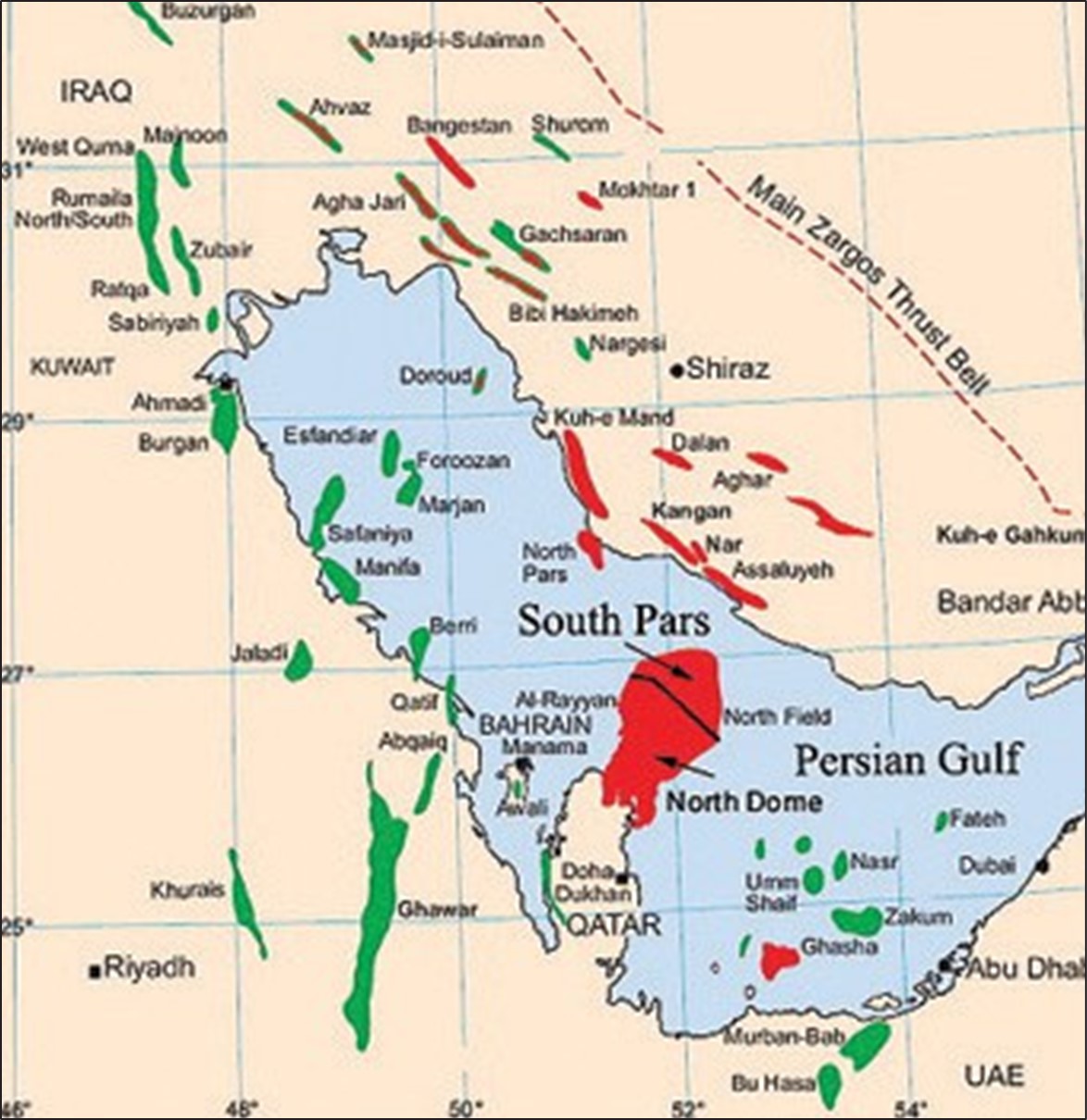
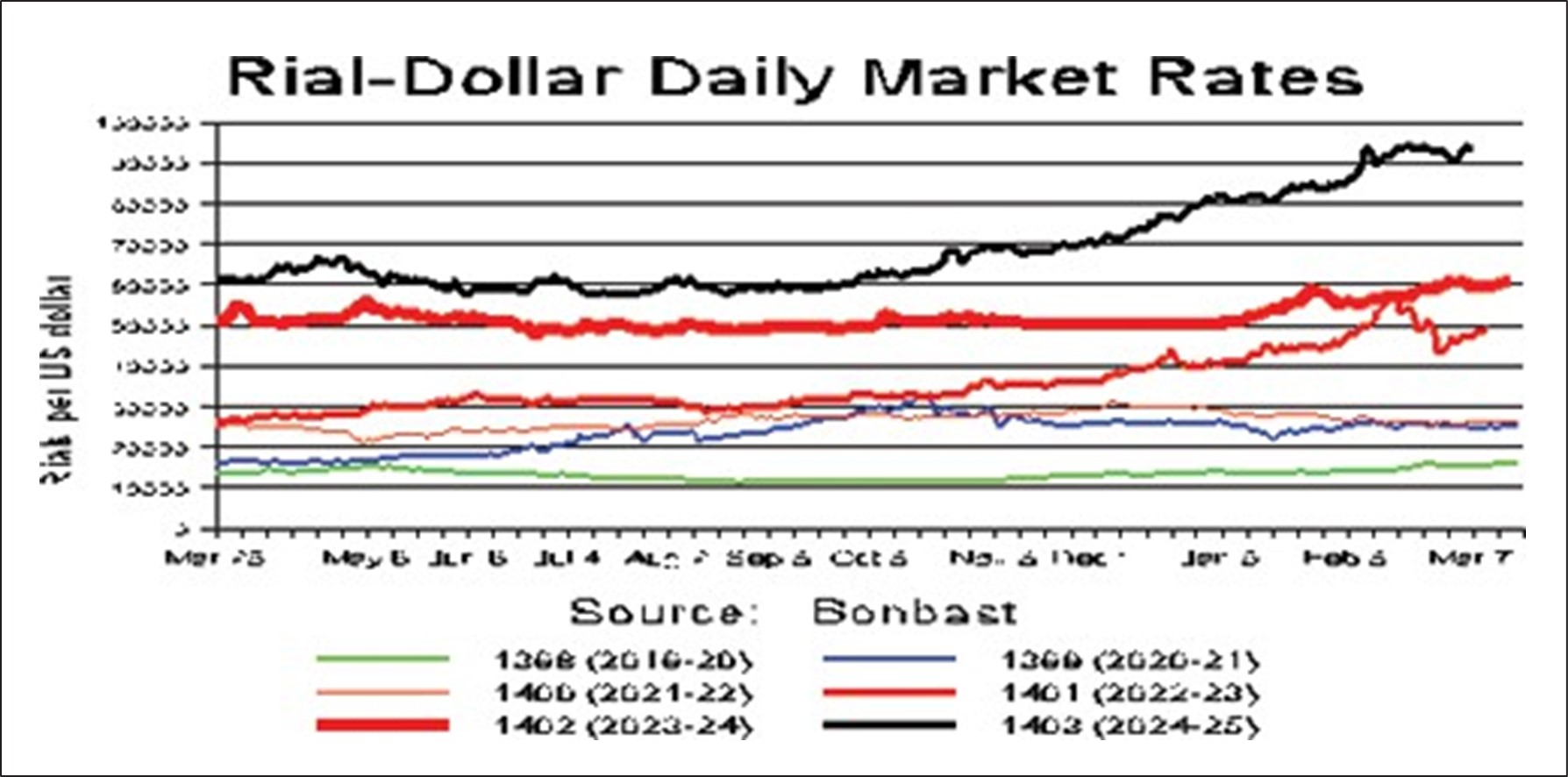
December 21, 2018
Computer hackers linked to Iran have been attempting to break into the private emails of nuclear scientists, the Associated Press reports.
A hacking group dubbed Charming Kitten has reportedly spent the past month trying to obtain access to the scientists’ messages, as well as those of US Treasury officials, Washington, DC, think-tank employees, and people involved in the nuclear negotiations.
“Presumably, some of this is about figuring out what is going on with sanctions,” said Frederick Kagan, a scholar at the American Enterprise Institute who was targeted.
The list surfaced after Charming Kitten mistakenly left one of its servers open.
They also targeted a nuclear scientist for Pakistan’s Ministry of Defense, a senior operator at the Research and Training Reactor in the Jordanian city of Ramtha, and a high-ranking researcher at the Atomic Energy Commission of Syria.
They also targeted Guy Roberts, the US assistant secretary of defense for nuclear, chemical, and biological defense programs. “This is something I’ve been worried about,” Roberts said.
The AP drew on data gathered by the London-based cybersecurity group Certfa to track how Charming Kitten spent the past month. Researchers at Certfa found the server and extracted a list of 77 Gmail and Yahoo addresses targeted by the hackers that they handed to the AP for further analysis. Although those addresses likely represent only a fraction of the hackers’ overall effort — and it’s not clear how many of the accounts were successfully compromised — they still provide considerable insight into Tehran’s espionage priorities.
“The targets are very specific,” Certfa researcher Nariman Gharib said.
In a report published December 13, Certfa tied the hackers to the Iranian government, a judgment drawn in part on operational blunders, including a couple of cases where the hackers appeared to have accidentally revealed that they were operating from computers inside Iran. The assessment was backed by others who have tracked Charming Kitten. Allison Wikoff, a researcher with Atlanta-based Secureworks, recognized some of the digital infrastructure in Certfa’s report and said the hackers’ past operations left little doubt they were government-backed. “It’s fairly clear-cut,” she said.
Another of Charming Kitten’s targets was Andrew J. Grotto, whose tenure on the US National Security Council in the White House straddled the Obama and Trump Administrations. Jarrett Blanc, the State Department coordinator responsible for the implementation of the nuclear deal under Obama, was also on the list.
The list indicates that Iranian spies were also interested in US defense companies. One of those targeted is a senior director of “breakthrough technology” at the aerospace arm of Honeywell International Inc., the New Jersey-based industrial conglomerate; another is a vice president at Virginia-based Science Applications International Corp., a prominent Pentagon contractor.
An analysis of Certfa’s data shows the group targeted at least 13 US Treasury employees’ personal emails, including one belonging to a director at the Financial Crimes Enforcement Network (FinCEN), which fights money laundering and terror financing, and one used by the Iran licensing chief at the Office of Foreign Assets Control (OFAC), which is in charge of enforcing US sanctions. But a few employees’ LinkedIn profiles referenced back office jobs or routine tax work. That suggested “a fairly scattershot attempt,” said Clay Stevenson, a former Treasury official who now consults on sanctions and was himself targeted by Charming Kitten.
Another Charming Kitten target was an intern working for the Foundation for Defense of Democracies, a Washington think tank that has been one of the Iran deal’s fiercest critics. How the intern — whose email isn’t public and whose name appears nowhere on the organ-ization’s website — got on the hackers’ radar is unknown.