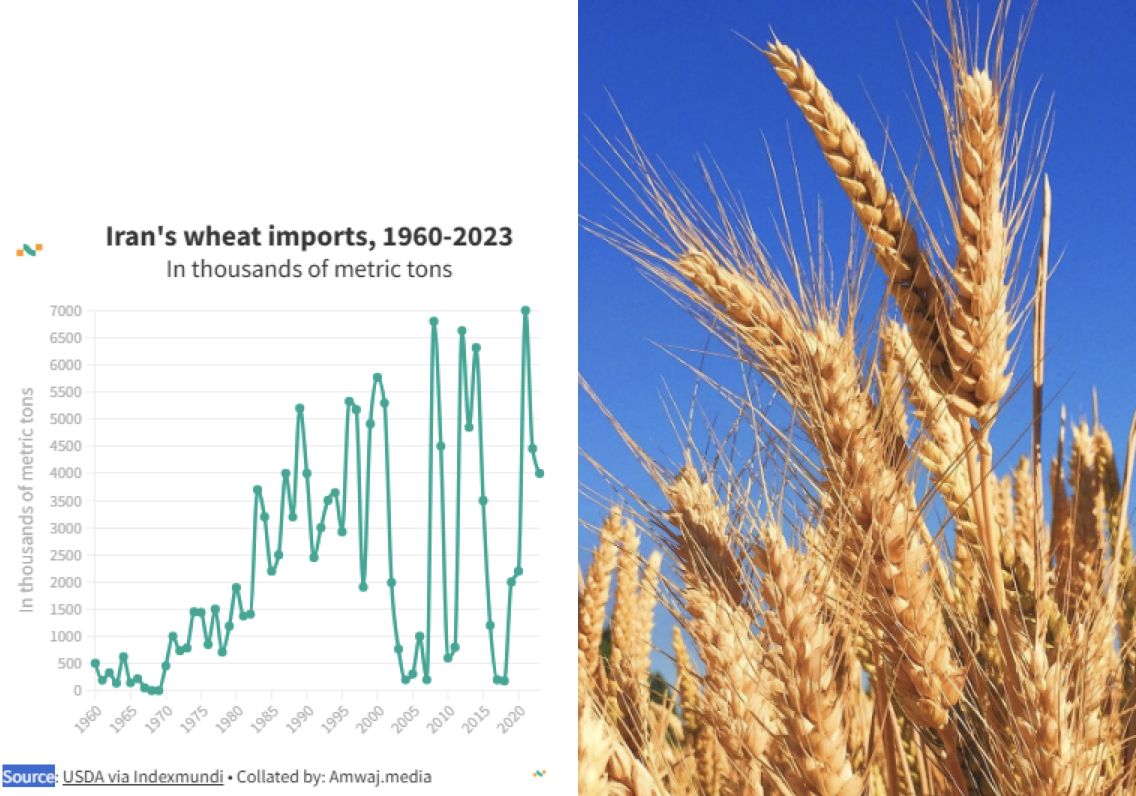
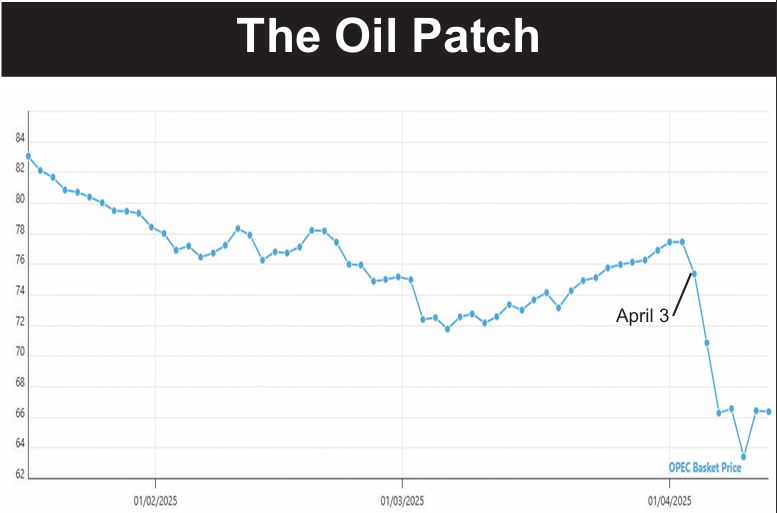
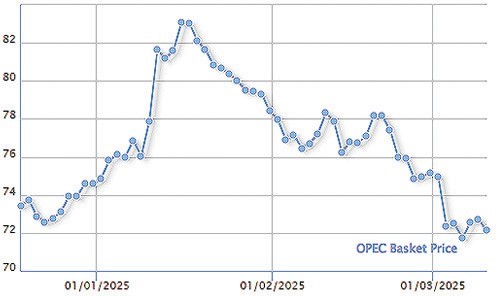
from the Iranian Foreign Ministry and shut down its website for several hours.
The published documents are not high policy—or even low policy—revelations, but involve applications from foreigners seeking visas to visit Iran.
The decentralized, loosely connected hacker group broke into the email center of the Iranian Passport and Visa Office last week during what it called “Operation Iran.” An online user of the #OpIran channel, presumed to be involved in the attack, said the operation “is a multi-site incursion using a variety of exploits and hand-crafted methods.”
The 10,365 leaked emails can now be downloaded from hosting websites and protocols such as MediaFire and BitTorrent. Most of them, an unnamed source told International Business Times, are from Iranian government officials regarding visa requests from non-Iranians to attend “an oil meeting.”
“Many” involve applicants from China enquiring about their application status. Because the ministry’s website requires images of applicant passports and other documents, without providing sufficient space for the files (only 40KB can be uploaded), many of the emails include exchanges seeking to remedy the insufficient images submitted.
One Anonymous member said the goal of “Operation Iran” was to damage Iran’s image online and off-line. Iranian officials, in response, have tried to conceal any reports of the breach and made no comment on the temporary shutdown of the ministry website.
Anonymous, which began to move from hacking for entertainment to “hacktivism” over the last few years, has begun to establish a legacy of disrupting autocratic regimes in North Africa and the Middle East.
It launched “Operation Iran” on May 1 with an announcement that it would stand with the people of Iran against the government’s oppression.