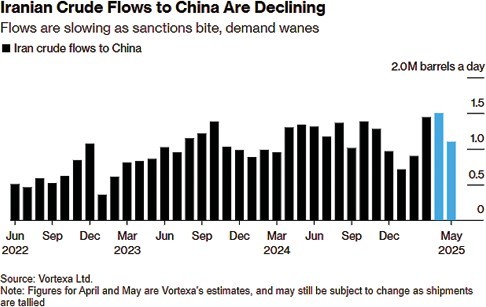
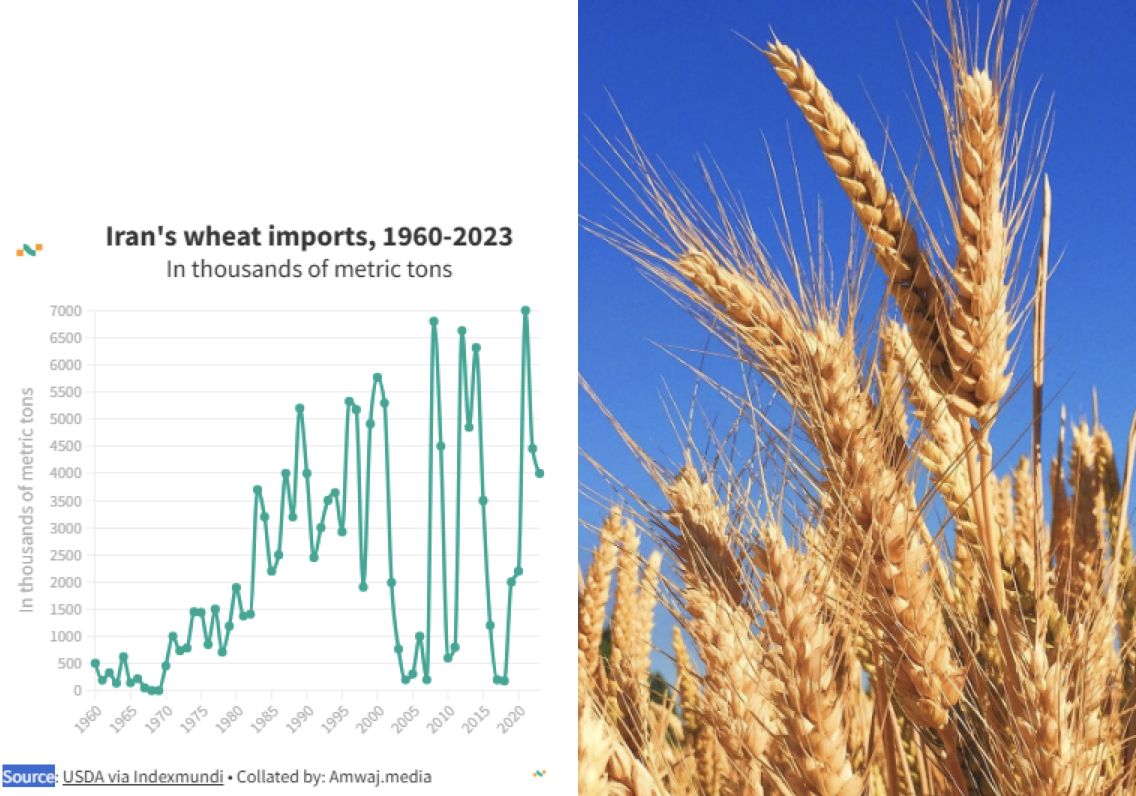
But it is the Islamic Republic that has been publicizing the Stars worm. Foreign computer security specialists have almost uniformly said they think Iran is just making it all up.
In fact, the real computer threat to Iran’s nuclear program may still be the Stuxnet worm—and Iran is now acknowledging that.
Gen. Gholam-Reza Jalali, who heads the military agency to counter foreign sabotage and cyber attacks, announced four weeks ago that Iran had been the target of a second, post-Stuxnet, cyber attack.
Jalali gave hardly any information beyond saying the worm in the latest attack is called “Stars.” Jalali said Stars was an “espionage virus.” He didn’t identify any sites that had been infected. Nor did he say what Stars did to computers it has infected.
In Europe and North America, computer security experts pooh-poohed Jalali’s allegations. They pointed out that no specifics have been produced on the Stars worm. (See Iran Times of May 6, page 10.)
When the Stuxnet worm hit Iran, copies of the worm were widely distributed and were available for analysis. A month after Jalali described the Stars worm attack, the Islamic Republic has made not one scintilla of evidence available to analysts abroad.
But despite that, last week Communications Minister Reza Taqipur acted as if it was the West that was talking about the Stars threat. He told reporters last week that all the chatter about Stars was part of a psychological warfare offensive by the West against Iran.
While most media attention has focused on Jalali’s Stars assertion, more important was what Jalali said April 25 about Stuxnet while announcing the alleged Stars attack.
Until now, Iranian officials have uniformly proclaimed that Iranian experts had completely expunged Stuxnet from Iran and eliminated any threat from it.
Jalali said just the opposite.
He said Stuxnet still poses a potential risk. “We should know that fighting the Stuxnet virus does not mean the threat has been completely tackled, because worms have a certain life span and they might continue their activities in another way.”
Indeed, a number of computer specialists in the West have said Stuxnet appears to be designed to hide itself and lie dormant for a time before attacking again.
David Albright, a nuclear weapons specialist, has said Stuxnet was designed to continue operating through 2012 and could remain dormant inside Iranian computers until activated by remote command.